Quick intro
BitLocker is like backup. It’s good to have it. It’s better to have the restore verified as well.
If you’re planning to implement BitLocker into your organization (or already have that), it’s good to know what’s the choice of storing the recovery password:
- save to a file - either usb stick or unc share
- backup to ActiveDirectory
- backup to Azure ActiveDirectory
- use MBAM
More information can be found here.
For me, the best approach would be to:
- use GPO to encrypt end user device AND store the password in Active Directory
This can be configured here:
Computer Configuration -> Policies -> Administrative Templates -> Windows Components -> BitLocker Drive Encryption -> Store BitLocker recovery information in Acive Directory Domain Services.
This also ensures that encryption won’t start if recovery key failed to be backed up to AD.
- use Intune and encrypt user device AND store the password in Azure Active Directory with self-service key recovery feature
This doesn’t introduce the cost of MBAM or SCCM.
What if you already have your drives encrypted, and now want to improve the process of recovering information? As always - PowerShell to the rescue. To send information to AD we can use Backup-BitLockerKeyProtector. It can accept either KeyProtectorID or the ID itself. Retrieving those is simple.
Ways to get BitLocker recovery key information to AD and Azure AD
Manage-BDE
We can get the information using manage-bde tool:
-
Retrieve information
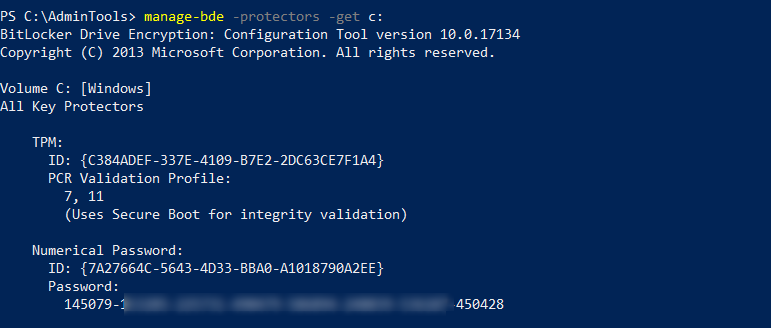
-
Send to AD
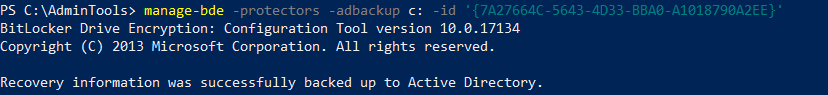
PowerShell
This is more fun (objects not strings!). Let’s first get information about our volumes:
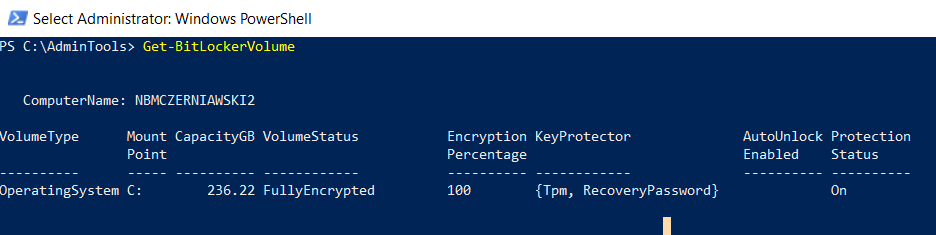
As you can see I have only one drive, encrypted with TPM. To get the same information as before let’s select-object
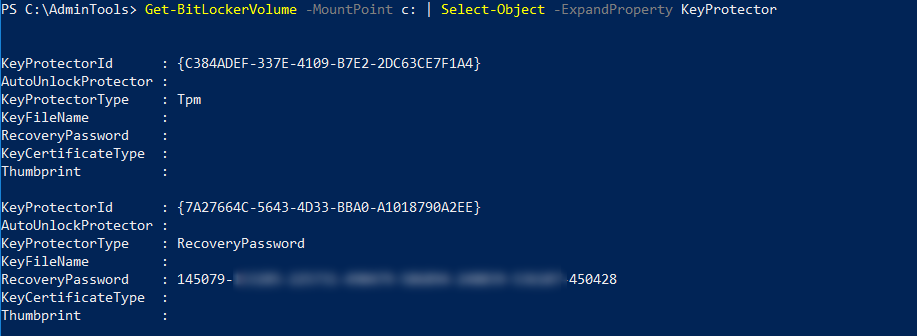
This returns two objects for each drive. We’re interested in the second object
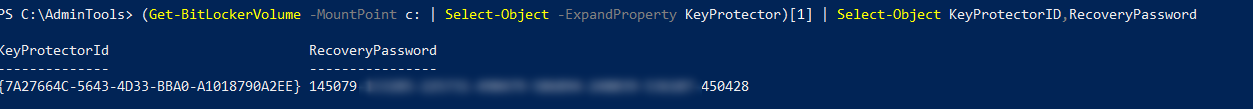
Active Directory
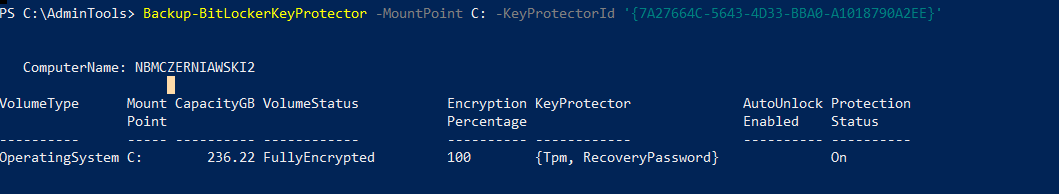
Let’s store the information to ActiveDirectory now:
If I would have more drives, this would come in handy:
$BitLockerVolumes = Get-BitLockerVolume
foreach ($blv in $BitLockerVolumes) {
Backup-BitLockerKeyProtector -MountPoint $blv.MountPoint -KeyProtectorId (($blv.KeyProtector)[1] | Select-Object -ExpandProperty KeyProtectorID)
}
ComputerName: NBMCZERNIAWSKI2
VolumeType Mount CapacityGB VolumeStatus Encryption KeyProtector AutoUnlock Protection
Point Percentage Enabled Status
---------- ----- ---------- ------------ ---------- ------------ ---------- ----------
OperatingSystem C: 236.22 FullyEncrypted 100 {Tpm, RecoveryPassword} On
Update 2019-04-23
For this above to work you have to be:
- AD User
- Member of local adminstrators on your machine.
That is not a desirable configuration ![]()
And using Invoke-Command to remote machines will fail too.
To fix this you will have to delegate proper permissions to SELF object:
- Right click on root domain:
- Click
Next, ClickAdd, typeSELFthenCheck NamesandOK
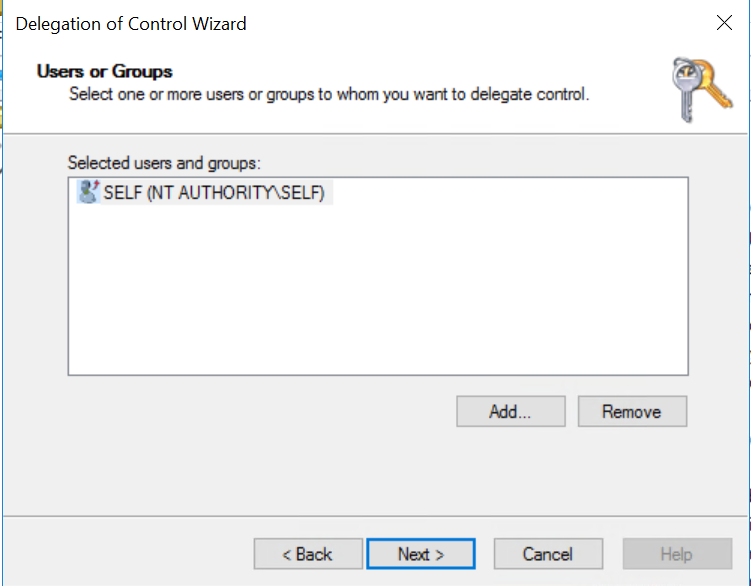
- Click
Next,Create a custom task to delegate,Next, selectOnly the following object in the folderand selectComputer ObjectsthenNext - De-Select
Generaland SelectProperty-Specific.
Then from the list selectWrite msTPM-OwnerInformationand clickNext - Finish the wizard
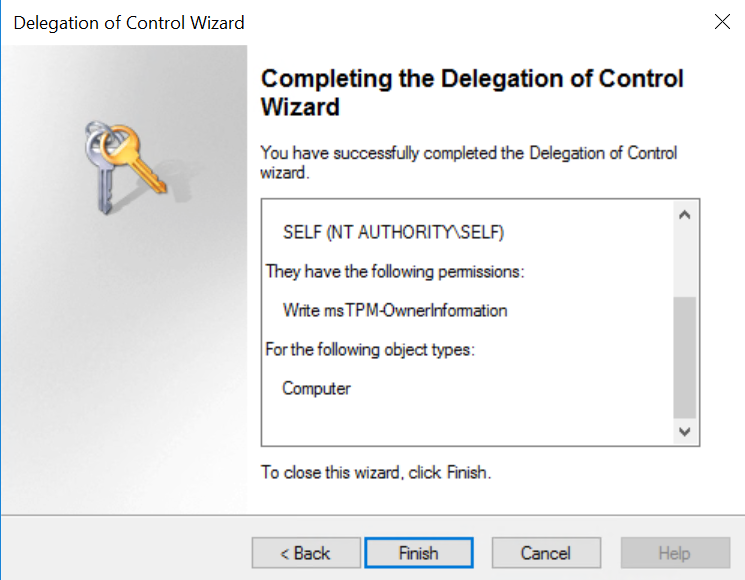
This will allow to use both Invoke-Command to remotely (in automated way) store all BitLocker Keys in ActiveDirectory!
More information can be found here.
Azure Active Directory
Same goes with sending RecoveryKey to Azure AD, this time with BackupToAAD-BitLockerKeyProtector:
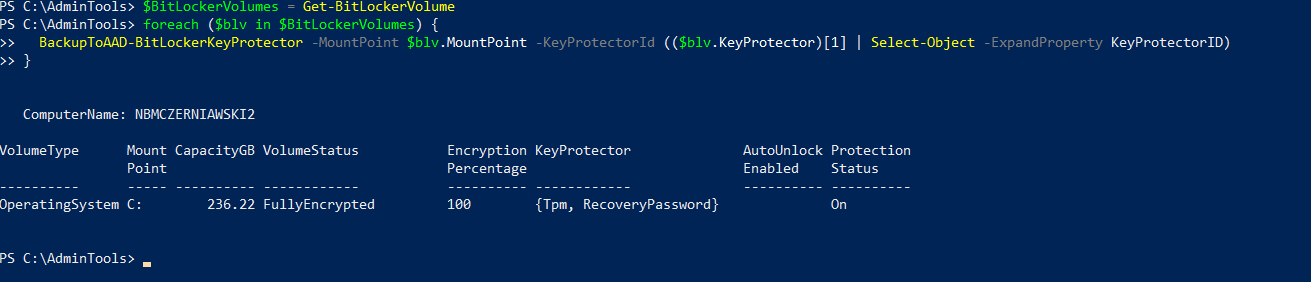
$BitLockerVolumes = Get-BitLockerVolume
foreach ($blv in $BitLockerVolumes) {
BackupToAAD-BitLockerKeyProtector -MountPoint $blv.MountPoint -KeyProtectorId (($blv.KeyProtector)[1] | Select-Object -ExpandProperty KeyProtectorID)
}
ComputerName: NBMCZERNIAWSKI2
VolumeType Mount CapacityGB VolumeStatus Encryption KeyProtector AutoUnlock Protection
Point Percentage Enabled Status
---------- ----- ---------- ------------ ---------- ------------ ---------- ----------
OperatingSystem C: 236.22 FullyEncrypted 100 {Tpm, RecoveryPassword} On
Retrieve RecoveryKey
From Active Directory
Now the best part - how to get the information back. Since Windows 2008 BitLocker Recovery Key is stored in AD in msFVE-RecoveryInformation objectclass aassociated to Computer. To get that we first need to get Computer Object and then search Active Directory for ObjecClass of given type. This is assuming your account have rights to read the information from AD in the first place! (great article here)
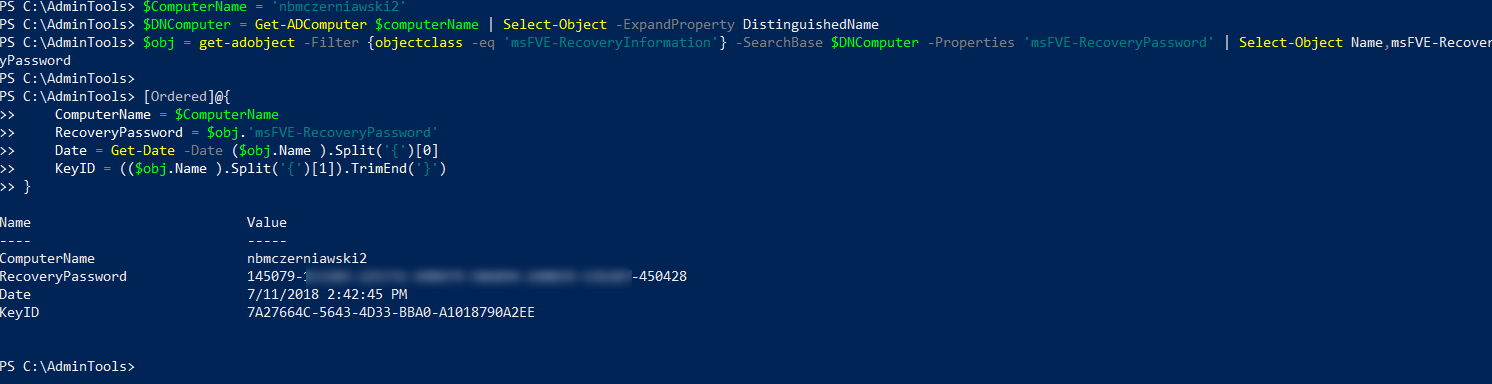
I’m using custom objects for better readability. The date shows when the drive was encrypted!, not when the information was backed up.
From Azure AD
There is a delay between using BackupToAAD-BitLockerKeyProtector and the information showing on AzureAD. Give it time to synchronize :)
Navigate to https://myapps.microsoft.com, go to the Profile page and see all the registered devices:
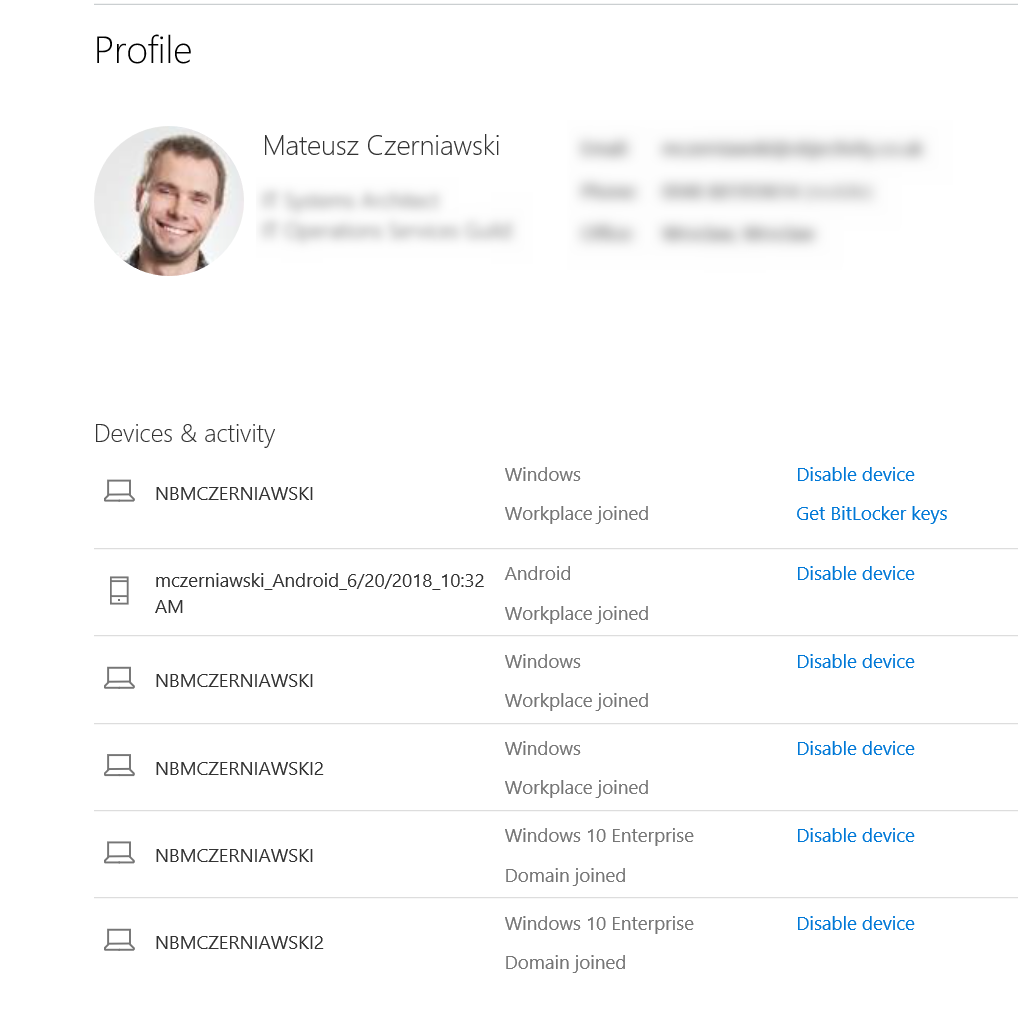
From there You can view the recovery password for You devices. Btw - it’s not very intuitive - You cannot access this informatorom directly from office.com -> profie pages.